Common Smart Contract Design Mistakes (That Kill Projects in Production)
DAte
Jan 22, 2026
Category
Smart Contract
Reading Time
5 Min
There's a moment every smart contract developer experiences: you deploy to mainnet, users start interacting with your contract, and then you see it. The transaction that shouldn't be possible. The edge case you didn't consider. The exploit you never imagined. And there's nothing you can do because the contract is immutable.
Smart contracts are unforgiving. In traditional software, you can patch bugs. In smart contracts, bugs are permanent features. This changes everything about how you need to design them.
Let's talk about the mistakes that kill projects in production—not theoretical vulnerabilities from security papers, but the actual errors that have cost hundreds of millions of dollars and destroyed companies. Because learning from other people's disasters is much cheaper than creating your own.
Mistake #1: Assuming External Calls Are Safe
The Error: Calling external contracts without protecting against reentrancy or malicious behavior.
Why It Kills You: External contracts can execute arbitrary code, including calling back into your contract before the first call finishes. The infamous DAO hack worked this way—a recursive call drained $60M before the contract could update balances.
The Fix:
Better: Use OpenZeppelin's ReentrancyGuard. Don't try to be clever with security.
Mistake #2: Not Handling Failed Transfers
The Error: Assuming ETH transfers always succeed.
Why It Kills You: Contracts can reject ETH by reverting in their receive function. If your contract logic depends on sending ETH and doesn't handle failures, your entire contract can become bricked.
Real Example: King of the Ether Throne—players became "king" by sending more ETH than the previous king, who got refunded. Someone deployed a contract that rejected ETH, became king, and broke the entire game because refunds started failing.
The Fix:
Lesson: Never make critical logic depend on successful external transfers. Use pull payments instead of push payments.
Mistake #3: Integer Overflow/Underflow Ignorance
The Error: Not protecting against arithmetic overflow and underflow (pre-Solidity 0.8.0).
Why It Kills You: If a uint256 holding the max value (2^256-1) gets +1, it wraps to 0. Attackers can manipulate balances, mint unlimited tokens, or drain funds.
Real Example: Multiple token contracts allowed attackers to underflow balances, giving themselves unlimited tokens.
The Fix:
Lesson: Use Solidity 0.8.0+ for automatic checks, or SafeMath for older versions. Never do arithmetic without overflow protection.
Mistake #4: Weak Access Control
The Error: Anyone can call admin functions because you forgot onlyOwner modifier.
Why It Kills You: Attacker calls transferOwnership, pause, mint, or withdraw and drains the contract or takes control.
Embarrassing Reality: This happens in production more often than you'd think. Unprotected admin functions are shockingly common.
The Fix:
Lesson: Every privileged function needs access control. Use established patterns from OpenZeppelin, not homegrown solutions.
Mistake #5: Front-Running Vulnerabilities
The Error: Not accounting for MEV (Miner Extractable Value) and transaction ordering attacks.
Why It Kills You: Attackers see your transaction in the mempool, submit their own with higher gas, and exploit price changes, oracle updates, or ordering dependencies before your transaction executes.
Real Example: DEX trades get front-run constantly. Attacker sees your large buy order, buys before you (pushing price up), then sells to you at the higher price.
The Fix:
Lesson: Assume all pending transactions are visible to attackers. Include slippage protection, use commit-reveal schemes, or leverage privacy solutions.
Mistake #6: Unbounded Loops and Gas Limits
The Error: Loops that iterate over growing arrays without gas limits.
Why It Kills You: As the array grows, eventually the loop costs more gas than the block limit. Your function becomes permanently unusable.
Real Example: Governance contracts that iterate over all token holders. Once you have 10,000+ holders, voting functions exceed block gas limits and become uncallable.
The Fix:
Lesson: Never iterate over unbounded arrays in a single transaction. Use pagination or pull patterns instead.
Mistake #7: Timestamp Dependence
The Error: Using block.timestamp for critical logic, assuming it's accurate.
Why It Kills You: Miners can manipulate timestamps within a ~15 second window. For time-sensitive operations (auctions, lotteries, vesting), this enables exploitation.
The Fix:
Lesson: Block numbers are safer than timestamps. For critical timing, consider oracles or accept that timestamps have ~15 second variance.
Mistake #8: Not Planning for Upgrades
The Error: Deploying immutable contracts with no upgrade path when requirements will change.
Why It Kills You: You find a bug, need a new feature, or regulations change. You're forced to deploy a new contract and migrate all users and state—expensive and often impossible.
The Fix:
Lesson: For anything complex or long-lived, use upgradeability patterns. OpenZeppelin's upgradeable contracts library is your friend.
Mistake #9: Trusting User Input
The Error: Not validating inputs, assuming users will only call functions correctly.
Why It Kills You: Users (or attackers) will call your functions with edge case values: 0, max uint, addresses that don't exist, malicious contract addresses.
The Fix:
Lesson: Validate everything. Check ranges, verify addresses aren't zero, ensure amounts make sense. Emit events for all state changes.
Mistake #10: Insufficient Testing
The Error: Testing happy paths only, not edge cases and attack scenarios.
Why It Kills You: Production is where attackers test your edge cases—with real money on the line. Every untested code path is a potential exploit.
What You Need:
Unit tests: Every function, every branch
Integration tests: How contracts interact
Fuzzing: Random inputs to find edge cases
Formal verification: Mathematical proofs for critical functions
Multiple security audits: Different firms catch different issues
Bug bounties: Pay white-hats to find vulnerabilities
Reality Check: Companies like Base58 (base58.io) spend 40-60% of development time on testing and security for production contracts. That's not overkill—that's professionalism when handling real value.
The Meta-Mistake: Rushing to Production
Every mistake above is compounded by one meta-error: deploying too quickly.
The pressure is real:
Investors want launches
Marketing wants dates
Competitors are shipping
The team wants to ship
But rushing kills projects. Take time to:
Write comprehensive tests
Get multiple security audits
Run bug bounties
Deploy to testnets for weeks
Start with low TVL limits
Build emergency pause mechanisms
Base58 has seen projects lose months of work and millions of dollars because they skipped one security audit or didn't test edge cases thoroughly. The cost of delay is real, but it's nothing compared to the cost of a critical exploit.
What Professional Smart Contract Development Looks Like
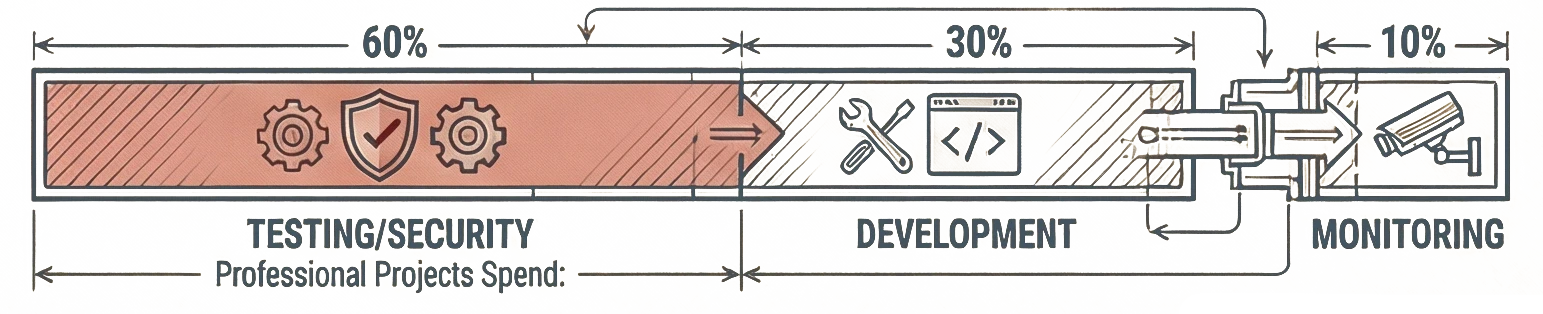
Here's the reality of production-grade smart contract development:
60% Testing and Security: Unit tests, integration tests, fuzzing, formal verification, multiple audits
30% Development: Writing the actual contract logic
10% Deployment and Monitoring: Mainnet deployment, monitoring, incident response
If that seems backwards, you're thinking like a web developer. Smart contracts aren't web apps. They're financial infrastructure handling millions of dollars with no undo button. The bar is higher.
At Base58, we've built our smart contract development process around preventing exactly these mistakes. We've seen what goes wrong when teams skip security audits, rush testing, or ignore edge cases. Our approach prioritizes security from day one because we know that in smart contracts, you only get one chance to get it right.
Our smart contract development includes:
Comprehensive security audits before any mainnet deployment
Extensive testing coverage including fuzzing and formal verification
Established patterns using battle-tested libraries like OpenZeppelin
Emergency response planning with pause mechanisms and upgrade paths
Continuous monitoring after deployment to catch issues immediately
We don't cut corners on security because we've seen the cost of shortcuts. When you're handling real value, the difference between thorough development and rushed deployment is often the difference between success and catastrophic failure.
Conclusion
Every mistake in this article has destroyed real projects and cost real money. The DAO. Parity. Poly Network. Countless smaller projects that lost everything to preventable bugs. The good news: these mistakes are well-documented and preventable. The patterns and solutions exist. You don't need to reinvent security—you need to learn from disasters that already happened and apply established best practices.

Leo Park
Blockchain Expert